昔CISSP研修でRBACの管理方法が4種類あることを学んだが、
・非RBAC
・制限RBAC
・ハイブリッドRBAC
・完全RBAC
温故知新のためSaliPointやNIST(米国国立標準技術研究所)のサイトを調べたのでメモします。
What is Role-Based Access Control (RBAC)?
Role Based Access Control RBAC
Role-based Access Control: an Overview

基本概念






The NIST standard includes four RBAC models:

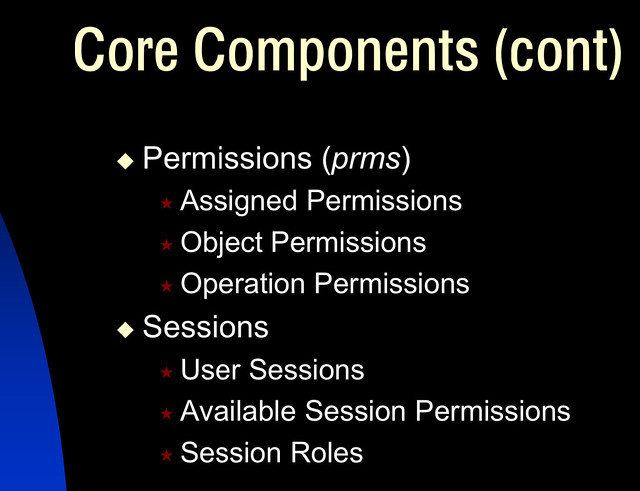
The basic model has three elements: users, roles, and permissions. The model design is based on the "many-to-many" principle, meaning that more than one user can have the same role and one user can have multiple roles. Likewise, you can assign the same permission to multiple roles and assign the same role to multiple permissions.
Core RBAC defines a minimum collection of RBAC elements, element sets, and relations in order to completely achieve a Role-Based Access Control system. This includes user-role assignment and permission-role assignment relations, considered fundamental in any RBAC system. In addition Core RBAC introduces the concept of role activation as part of a user's session within a computer system. Core RBAC is required in any RBAC system, but the other components are independent of each other and may be implemented separately.

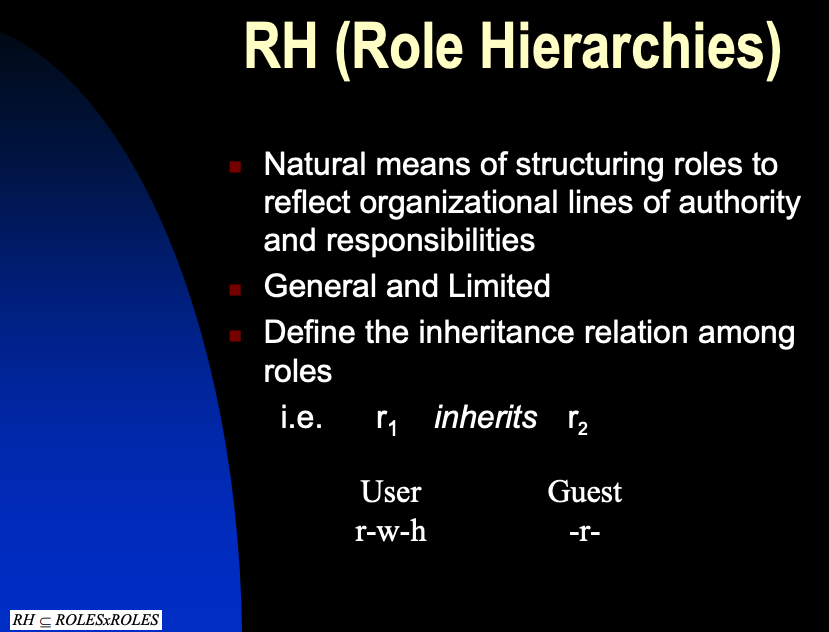
Adds a fourth component, hierarchy, which defines seniority relations between the various roles. By enabling senior roles to automatically acquire the permissions of the junior roles, you eliminate redundancies such as having to specify certain permissions when roles overlap.
Hierarchical RBAC adds relations for supporting role hierarchies. Hierarchical RBAC goes beyond simple user and permission role assignment by introducing the concept of a role's set of authorized users and authorized permissions.



To help in situations when you have conflict of interest policies, relations among roles are added based on user assignments. For example, a user who is a member of one role would not be able to be assigned membership to a role that has a conflict of interest.
Static Separation of Duty Relations adds relations among roles with respect to user assignments. Because of the potential for inconsistencies with respect to static separation of duty relations and inheritance relations of a role hierarchy, the SSD relations model component defines relations in both the presence and absence of role hierarchies.
Like SSD, DSD limits available user permissions but is based on a different context. For example, a user may require a different level of access based on the task performed during the session, and DSD restricts the permissions that are activated during that session.
The fourth model component, Dynamic Separation of Duty Relations, defines relations with respect to roles activated as part of a user's session.

SSDはUAとRHで、DSDはSessionですね。
なお、SailPointのページにベストプラクティスも書いてあったので参考にします。
実際に大企業の場合は、
・RH+SSD+DSD
・ハイブリッドRBAC
的な運用になるでしょうか。

Comments